Threat Intelligence – Importance and Benefits

What is Threat Intelligence?
Threat intelligence is all about the threat and how it affects the cyber domain. It is about understanding the cyber threats, comprehending the cyber threats, analyzing the cyber threats, and then acting against the cyber threats.
Threat intelligence sources include real-time cyber information, online open-source intelligence, human intelligence, technical intelligence, public sector information, or data from the dark and deep web.
These resources help an organization to respond to the increasing cyber threats by improving its vulnerability and defense capability against the existing and upcoming threats. In other words, threat intelligence helps the organization to evolve and stay ahead of cyberattacks.
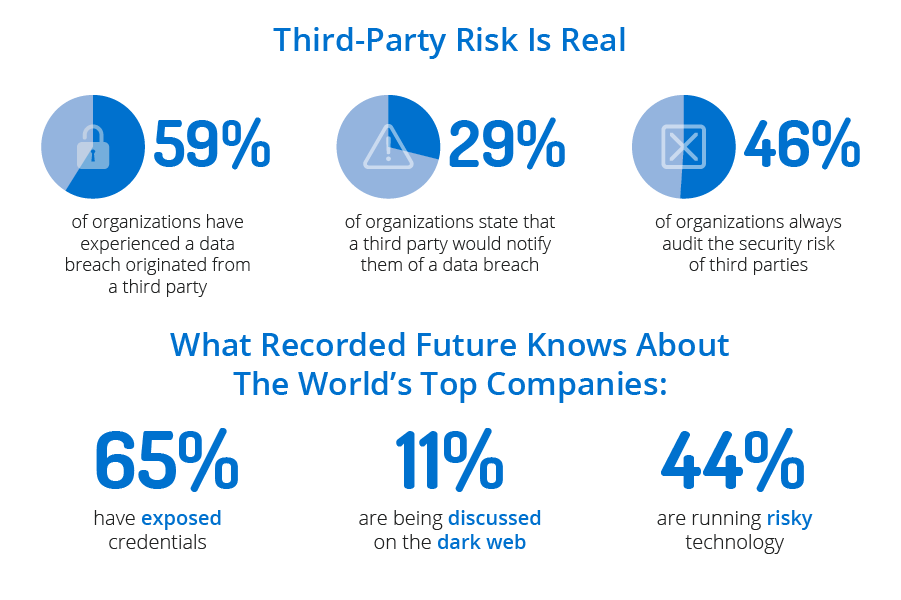
Nowadays, organizations across the globe are leveraging the power of threat intelligence to prevent, detect, and respond to emerging threats. These resources help an organization to proactively and intelligently deal with the evolving threats to its network, infrastructure, and software.
Traditional means of collecting such information about the threats have been outdated for a long time now. The benefits of using modern technology in this domain are:
– Traditional technical intelligence has been outdated for a long time. Today’s threat managers have to make do with very limited sources of technical intelligence. The traditional approach has been to collect information about the threats through research, investigation, and the analysis of computer code.
Modern threat intelligence depends on complex technologies like cyber investigations, malware reverse engineering, behavioral analytics, and digital signature technology. These technologies make it possible to understand the intent and purpose of malicious software.
– Detection and response are two important components of threat intelligence. Organizations need to take the appropriate steps to handle emerging vulnerabilities. This includes knowledge sharing, standardization of response, documentation for remediation, training and conducting incident response, usage of vulnerability management, and patching.
– Cyber threats intelligence must be predictive. Today’s IT managers are confronted with many complex and ambiguous IT issues. Cyber threats actors continue to develop new applications that can be exploited in unique ways.
Organizations have to proactively address the issues arising from the development of such attacks.
– Strategic cyber threats intelligence is necessary to counter and prevent attackers from getting a foothold in your network. For this, you need malware intelligence. Today there are complex and malware-ridden software programs that allow attackers to penetrate your network quickly and easily.
These programs also leave behind a trail of backdoors and other programs that make them highly difficult to detect or remove.
– Strategic cyber threats intelligence must be integrated with traditional technical intelligence. Traditional technical intelligence usually only targets known or predictable threat actors. These include nation-state and corporate attackers.
Cyber actors are still evolving so traditional technical intelligence will not always be applicable. You need a hybrid approach that takes into account the emerging nature of cyber threat actors and their ability to adapt to emerging vulnerabilities.
A combination of traditional threat intelligence plus proactive mitigation is the best way to secure your company and your network. In today’s world, when threat actors do not stay on the lookout for new vulnerabilities, they often use old ones as their weapons.
They use old and well-known tools to achieve their goals. By employing a combination of traditional and new threat intelligence techniques, you will be able to more readily detect and prevent threats from hurting your business.
– Traditional threat intelligence begins with understanding the typical activity of your competitors, such as their websites, emails, and social networks. You can then build a profile of these activities and attempt to gain an understanding of their intentions.
Once you have this information, you can begin developing counter-activity. Many times, these organizations will re-use known vulnerabilities in order to mitigate their own liability in the process.
– In addition to traditional threat intelligence, it is important to implement proper incident response procedures. Incident response involves working to mitigate the effect of any attacks or threats to your network.
There are many ways to respond to a security threat: blocking sources, changing configurations, and physically addressing the threat.
Proper incident response also involves communication with users and administrators to address any issues they may be experiencing and to make them aware of threats to their systems.
The development and implementation of the right threat intelligence and incident response procedures is crucial to the long-term security of your company.
Although there are a number of well-known techniques that can be used to mitigate a variety of cyber threats, it is also important for you to understand the risks you face and the best way to guard against them.
A solid understanding of what is cyber threats and the ways that these threats can affect your company can go a long way toward mitigating those risks. When you take the time to understand the way the world of cyberspace works, you will be able to prevent your company from being the next victim.
Why is threat intelligence so important?
The importance of threat intelligence is on the rise. This is one of the trends that most businesses follow these days. There is so much more to it than gathering the data and analyzing it.
It has to be a sound decision from the very beginning or else it will be lost. You do not want to miss the boat in terms of cyber threats because they can come up just as fast as they go down. These are the threats you need to watch out for.
Threat intelligence is also known as CTI or the commercial intelligence cycle, which is one of the major parts of the larger puzzle. The bigger picture is when it comes to securing your company’s network from malicious online attacks and activities.
When you look at the bigger picture, you will see that there are a lot of other things going on behind the scenes. You need to have a secure internet environment with firewalls, anti-spyware programs, and other types of security systems.
With all of this done, you will want to gather threat intelligence to monitor the activity that is going on to ensure everything is operating the way it should. There is also a whole sub category of this type of analysis known as forensic investigation.
You will take the evidence collected from hackers, malware, and other attacks, sort it out, and then analyze the results.
If you think about it, this all makes sense. You are trying to stop the attacks before they even begin. You have to get a grip on the attacks before you can put an end to them.
This is where threat intelligence comes in and why companies like BlockDos have put so much effort into making a data collection and analysis tool. The output product is a program that can detect malicious software, web exploits, phishing sites, and other attacks.
Most people do not realize that there are emerging threats that are much more advanced than most security systems can handle. It is becoming more common for hackers and programmers to create programs that work with a network of computers in order to bypass security systems.
While many security companies are working on ways to protect against newer threats, the truth is that some of the more basic vulnerabilities are still available. Companies using threat intelligence programs have to stay abreast of the latest threats so that they can keep their businesses protected.
The final step for companies using threat intelligence and data collection is for them to process the information. The intelligence program works by sending the captured information through a pre-existing infrastructure to make it usable by a security company. Processed data must be processed quickly and efficiently in order for it to be useful to an investigator or company that is looking to stop an attack.
Some companies use intelligence analysts to help them process data quickly in order to provide actionable intelligence. These analysts are responsible for analyzing captured data in order to provide investigators with the information they need.
These analysts work in teams and are usually stationed around the globe. They communicate with their counterparts all over the world in order to get the most accurate intelligence possible.
In order for one to be truly effective when combating cyber-attacks, it is important to have a variety of different sources of intelligence. Some intelligence comes from investigations, while other intelligence comes from dark web feeds, malware, and hacker forums.
The latter types of feeds only provide a glimpse into cyber-attacks, but they are great sources of information nonetheless. There are so many different sources of cyber-attacks, it is impossible to monitor all of them. However, the right intelligence analysts can use all of them in combination to find new ways to defend against cyber-attacks.
